- Products

Enjoy a free 30-day trial of our
data validation software.Experience the power of trusted data
solutions today, no credit card required! - Solutions

Enjoy a free 30-day trial of our
data validation software.Experience the power of trusted data
solutions today, no credit card required! - Partners

Enjoy a free 30-day trial of our
data validation software.Experience the power of trusted data
solutions today, no credit card required! - Learn more
- Pricing
- Contact Us
Hook, line and sinker: How to avoid phishing attacks

Not to be confused with fishing, no. Phishing refers to the stealing of personal information like usernames, passwords and credit card details that can lead to identity theft.
Phishing attacks are serious business and they, unfortunately, continue to advance in sophistication. If you fall victim to phishing attacks and unknowingly relinquish sensitive information to a cybercriminal, you can place your financial data at risk.
From a phisherman’s perspective, no account is off limits. Don’t fall victim to their attacks—read on to find out the different types of phishing scams and learn tips to avoid them.
Aside from the puns we can produce from the homophone, other horrors associated with phishing attacks lay in how cunning and widespread they are. Phishing can manifest in many forms, the most common of which is email.
To really stress why this can be bad news, consider these facts:
- Consumer email accounts make up 77 percent of worldwide email accounts.
- American companies send an average of 1.47 million emails per month.
- 72 percent of consumers say that email is their preferred medium of communication with companies they do business with.
- Over 205 billion emails were sent and received per day in 2015 and that number is projected to grow by three percent every year for the next four years.
Email is here to stay, and will only continue to increase in usage and importance. However, that only means more opportunities and greater incentives for cybercriminals to create malicious spam. For the most part, phishing is all about sending a massive amount of email in the hopes that unsuspecting recipients will click on links that will either download viruses onto their PCs or direct them to sham websites where they’ll be coerced into sharing personal information.
However, knowledge is security. Arming yourself with the knowledge of the different types of phishing scams will help you distinguish fact from fraud and hopefully prevent unnecessary financial consequences. The most common types are illustrated below.
1. Deceptive phishing
This is a type of phishing where there is a deliberate attempt to manipulate the recipient into giving up sensitive information. An example would be this fake PayPal email below where the reader is prompted to provide account information under the pretense of urgency.
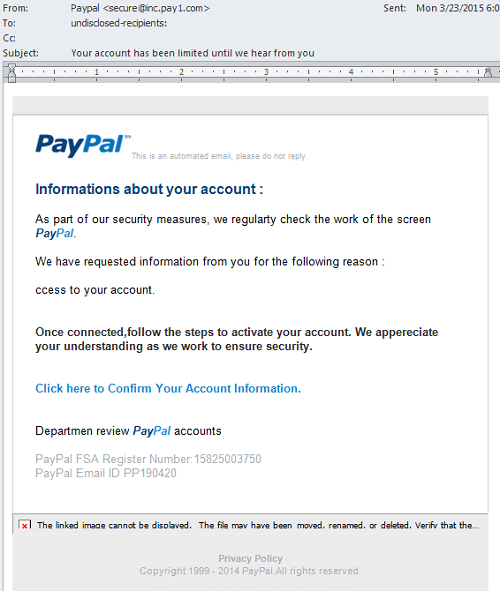
Other examples include emails about system failures requiring users to re-enter their information, false charges to your account and too-good-to-be-true offers.
2. Malware-based phishing
This is a type of phishing where the primary goal is to trick the user into downloading malicious software onto their computer. Malware phishing can be in the form of links, attachments or downloadable files from a website.
An example of a malware-oriented phishing scam is this fabricated Adobe Flash Player email where the possibility of a security risk drives users to download an actual security risk. We do see the irony.
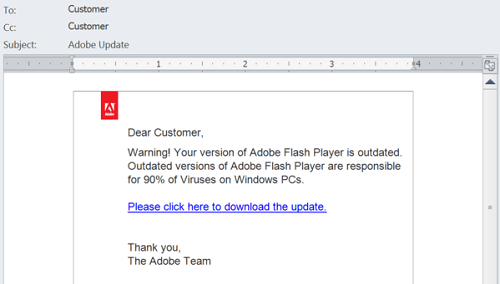
3. Social network website phishing
Thanks to the ubiquity of social media platforms, cybercriminals have yet another medium to scam people. Some examples include Twitter users receiving a message with attention-grabbing phrases such as, “You seen [sic] what this person is saying about you?” Clicking the link would direct them to a fake login page; if they entered in their credentials, an error web page is displayed and their account information is compromised.
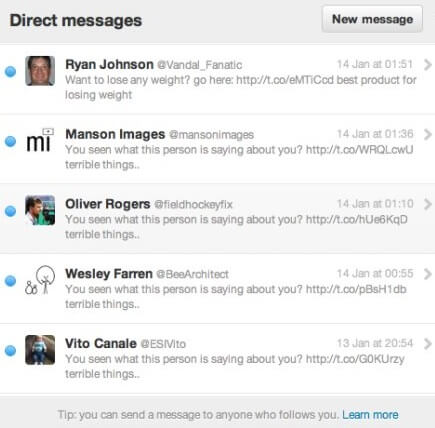
Another more malicious example of social network phishing is targeting users with emails claiming that their passwords have been reset. An attachment is given to the users to provide their updated information; however, when opened, a malware program then steals all passwords from the user’s PC.
4. Keylogging or screenlogging phishing
This type of phishing stems from free web utility programs that hide information-stealing malware. Once installed on the user’s computer, the malware can track keyboard input and browser sessions.
Examples of utility programs include:
- Virus protection
- Backup
- Data recovery
- Screen savers
5. Spear phishing
This type of phishing targets specific people as opposed to random groups of people. An example of this would be receiving an email from someone on your contact list urging you to click a link or download an attachment within.
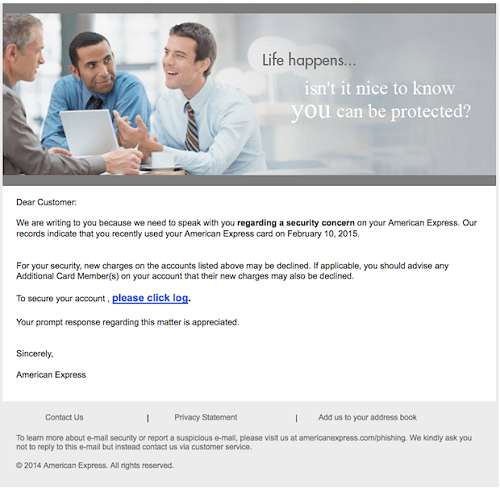
Once you fall victim to this, malware can be installed onto your PC or your login credentials can be stolen. This is particularly dangerous for users that have the authority to send checks or approve transfers within a company.
How to avoid falling hook, line and sinker for a phishing scam
Knowing the different types of phishing scams is the first step in preventing yourself from falling for one. Here are some tips you should follow to minimize that risk.
- Never enter information into an email with embedded submission forms.
- Never respond to emails threatening to close your account if you don’t take action; instead, go to the website of the company that is supposedly emailing you and call them.
- Poor grammar and spelling mistakes in an email that is strangely out of context almost always indicates a phishing scam.
- Do not click on links in emails that ask for your personal information.
- Do not download or open any attachments, even from familiar contacts, unless you are expecting them and know what they contain.
- Do not provide sensitive information to people who contact you out of the blue. Verify their identity by asking for their name, company, telephone number and address before relinquishing any information.
- Hover over the links provided to check that the URL destinations match the links provided.
In 9 out of 10 cases, you will be able to ascertain the legitimacy of emails simply through common sense. For the remainder of the times when phishing scams are a little harder to recognize, just carefully reading through the body of the email and following the best practices above will help you figure out whether or not the sender is trustworthy.
What’s also important is keeping you and your organization out of trouble with regulators. If you’re in possession of a purchased email list for whatever reason, not taking the time to validate those addresses can really damage your sender reputation and overall email campaigns—so keep an eye out for phishy emails!
Want to learn more about how the importance of your digital reputation?
- http://www.radicati.com/wp/wp-content/uploads/2013/04/Email-Statistics-Report-2013-2017-Executive-Summary.pdf
- http://www.cmocouncil.org/facts-stats-categories.php?category=direct-marketing
- http://www.emailisnotdead.com/
- http://www.radicati.com/wp/wp-content/uploads/2015/02/Email-Statistics-Report-2015-2019-Executive-Summary.pdf


